The [Wonderful] Start to the Season of Rigor...
(This blog post was migrated from my first, old, raw HTML/CSS/JS-only website.)
This post primarily covered some of my cool technical accomplishments during the intense MGHSCC CTF, as well as some other brief cyber or language-related activities. These all happened during a several-month period of intense productivity that I dubbed "The Season of Rigor".
SOME of what is and what will be going on in my computery-endeavors:
- Signed up for the Fall 2023 NCL CTF
- Joined OSINT-FR, and the DLI French Course
- Hitting "high dollar" challenges in Cyberstart, racking up points for the final stretch of the GHSCC season
Recent Governor's High School Cyber Challenge / Cyberstart Highlights
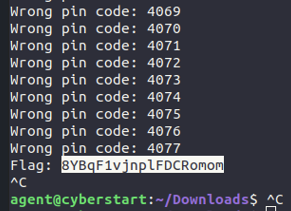
^Results of my following bruteforce script (with explanations):
#!/bin/bash
# I chose to use bash after I had some weird trouble with python
# Prompt: The program "prog-l0bar" takes an argument that is a four digit secret code. Crack it with a script.
for i in {0000..9999}
do
./prog-l0bar $i #pipes output and/or variable without "|"
done
# that's it!!
This was a super simple but cheeky-feeling way to finish a challenge :)
Some other things I've done to boost up to 82500 points (Rising 6000 or so points in just today, clearing the entirety of HQ level 9 [no easy feat!], now beating 8th place in the final 2018 Girls Go Cyberstart competition [ though I don't know how that translates to the GHSCC], and being 72.98% done [181/248 total challenges] with Cyberstart America) include Steganography with binwalk, more reverse engineering, and two particularly fun challenges that required some fun maneuvering:
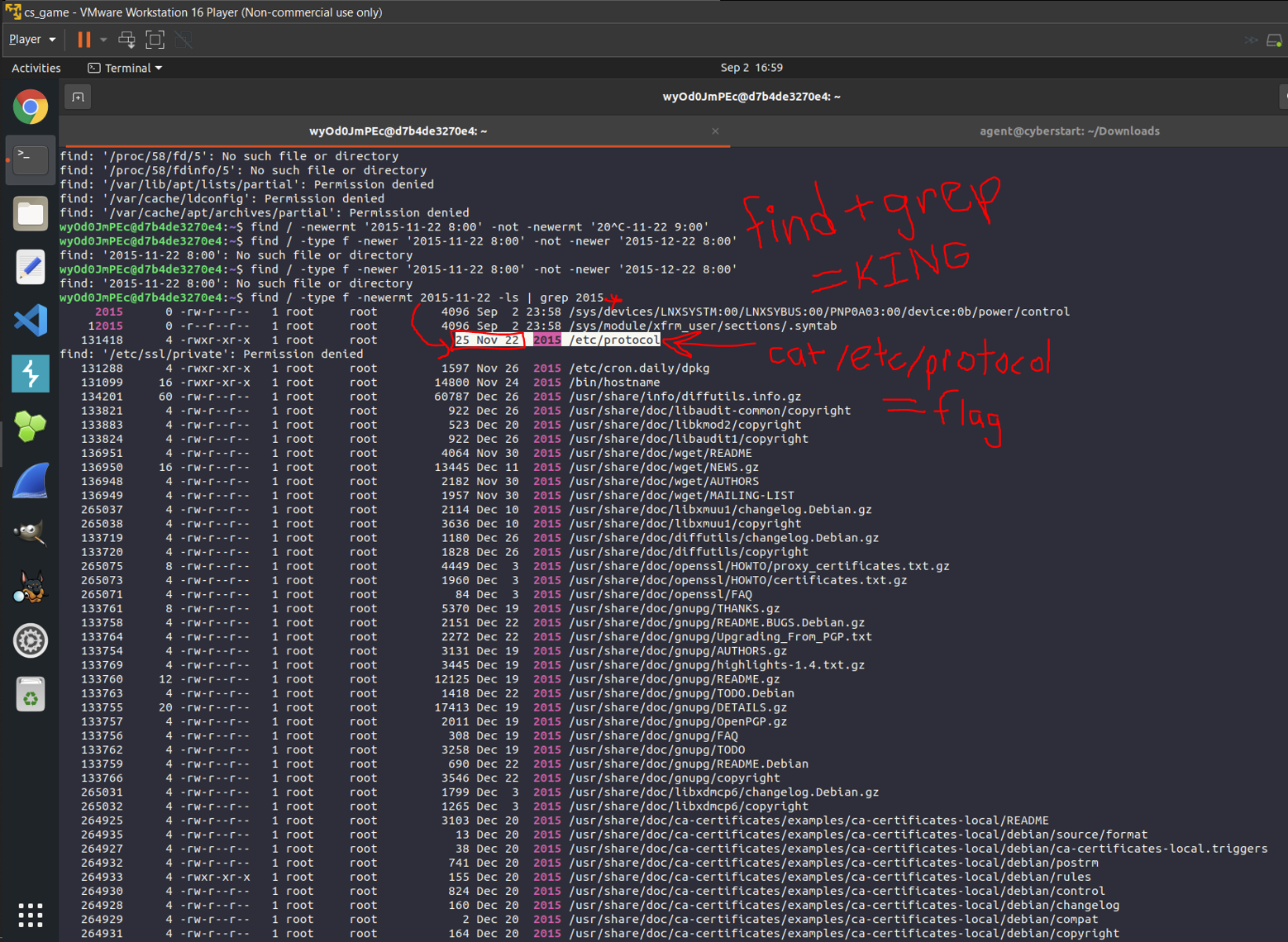
^Here, I had to ssh into a foreign system and find a nondescript file that was created November 22nd, 2015 at 20:00 (with no other information). After multiple tries and research, I found that I could use the deadly "find | grep" combo once again :)
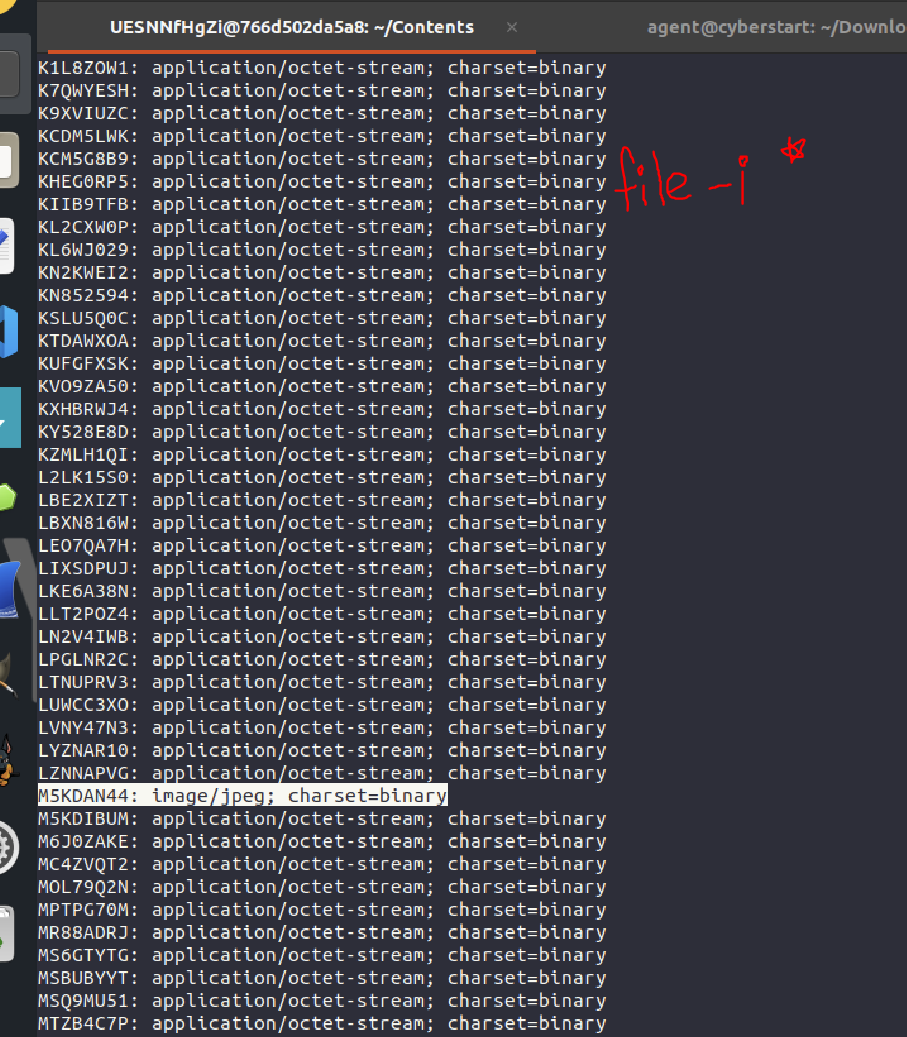
^The next challenge (the one I'm most proud of, and have probably cheesed/circumvented the hardest) required me to ssh into a remote system (remember, this gets rid of most fancy tools on your home system), and find an image file in a ginormous mix of junk files (with all of the files ends stripped).
This was no beginner level challenge, and you couldn't just cheesily use "strings" or "grep" to find some string that searched the file system for 'flag:' in one of the files, as the flag is in the actual rendered image. So, instead, I cheesily used "file -i *" to find the odd one out in the folder with all the junk files in it. That was part one of the challenge...
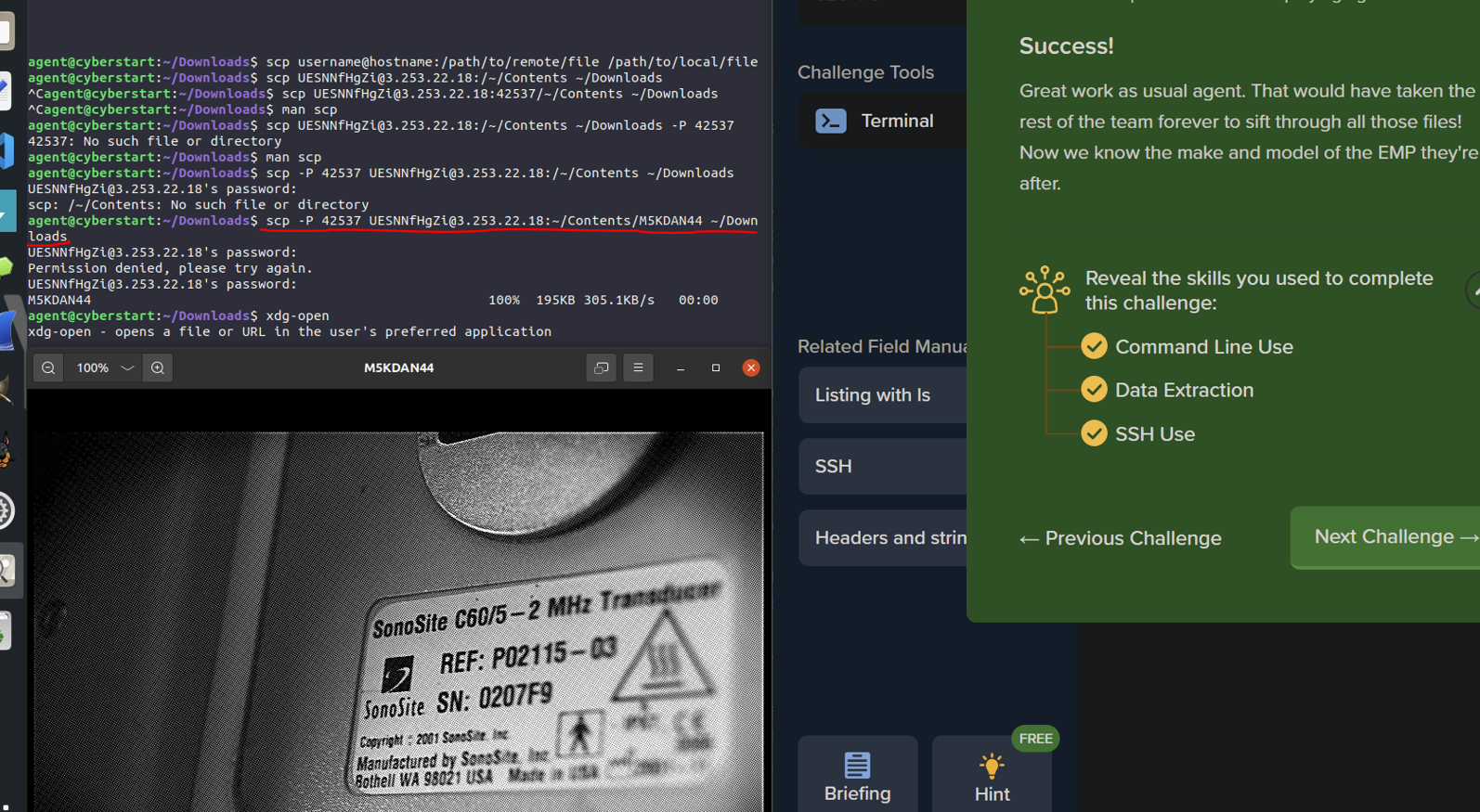
^Part two of the challenge required me actually rendering the image file to get the flag. But, because I was ssh'd into a limited remote system, it wasn't as easy as opening it with xdg-open, right clicking on it, or using an image viewer. So, I had to go throught he process of learning how to use the "scp" command to go from my home system, input the exact location of the file I just found with "file -i *" on the remote system, and take it back to my home system, where I could then render it with xdg-open. Voilà, the flag is the serial number (SN:0207F9) :)
OSINT-FR and DLI:
OSINT-FR Home Page Link I joined a global community of people curious about OSINT, both beginners and (primarily) super-whiz professionals and cyber ninjas, who do everything from develop powerful tools, share resources (online courses, neat articles, etc), tackle issues (e.g. disinformation, child abuse), and more! Au moins, ils parlent Français, et je peux les utiliser pour l'améliorer (particulierement avec la vocabulaire de Cybersécurité, et le web).
I also found some free resources online due to some OSINT of my own :) Those being free "FSI" (Foreign Service Institute) and "DLI" (Defense Language Institute) resources online for French, Spanish, and a myriad of other languages. I researched and judged the DLI course to suit my needs more, and will be partaking in that for the foreseeable future (it's designed to be 15-20 work weeks of 6 hour class days on the language).
Fall 2023 NCL CTF:
NCL Home Page Link Having participated in the Spring and Fall 2021 Individual Games, and the Fall 2021 Team Game, I can tell you that NCL is no joke. It has beginner to ultra-hard challenges in OSINT, Log Analysis, Network Traffic Analysis, Cryptography, Scanning, Forensics, Password Cracking, Enumeration and Exploitation, and Web Application Security (website hacking). This is going to be quite the competition, with me knowing much, much, MUCH more than I did than the last time I participated in this CTF. It's going to be fun :)
